
Adam Judd
Managing Director
Websites are under attack every day. Hackers, criminals, and others with malicious intent are constantly trying to find ways to break into websites and steal information or wreak havoc. If you run a website, it's essential to take steps to protect it from these threats. In this blog post, we will discuss why website security is essential and what you can do to safeguard your site.
A 'Wicked Problem' is challenging or impossible to address because of missing, contradictory, and changing requirements that are frequently hard to detect. It is a term that some may interpret to imply that a problem or situation is unsolvable since there isn't a simple solution, and "wicked" refers to resistance to resolution rather than evil.
Website security is a wicked problem because:
- The cyber security landscape is constantly changing and evolving, making it exponentially challenging to keep up.
- Website security is never "done"; it cannot be solved or fixed due to continuously emerging threats.
- The requirements for website security are often contradictory - for example, the need for security versus the need for usability.
Given that website security is a wicked problem, what can we do about it?
Organizations must continuously adapt their website security strategies to stay ahead of the threat as best they can. This means being proactive rather than reactive, constantly monitoring the threats, and taking steps to mitigate them.
Your Website Security is Important
Your website is the public digital face of your company. It's where customers learn about your products or services, often the first interaction they have with your brand. If your website is hacked or taken down, it can damage your reputation and cost you customers.
Who Hacks Websites?
Globally 30,000 Web Sites Hacked a Day*. Why? Because hackers can get access to a lot of personal information, or they could shut down the site entirely. Or, even worse, they could use your website as a launching pad to attack other websites.
*According to Kaspersky
There are many reasons why people hack websites. Some do it for political reasons, others simply for the challenge. But the vast majority of the reasons are for financial gain. Regardless of the motivation, however, all website hacks have one thing in common: they exploit vulnerabilities in the website's code or architecture.
There is a Low-level of entry – attacking websites doesn’t require specialised skills.
Most attacks are carried out by automated scripts or bots searching the Internet for vulnerable websites. These scripts can be very sophisticated, and they can launch an attack in minutes. The attackers don't even need to be exceptionally skilled; they just need to have access to the right tools.
However, some attacks are carried out by manual methods. These require more time and effort but can be much more damaging. For example, a targeted attack on a high-profile website could result in significant financial losses or reputational damage.
Hackers are indiscriminate in who they target – small businesses are just as much at risk as large corporations. Small businesses are often targeted because they tend to have weaker security than larger organisations.
Websites of all sizes and types can be hacked. There is no one profile of a target website. The only common denominator is that the site has vulnerabilities that the attacker has. They will use automated scanning tools to find these vulnerabilities or manually probe the site for weaknesses.
Website attacks are predominately financially motivated. Criminals hack websites to steal personal information like credit card numbers and login credentials. They can then use this information to commit fraud or sell it on the black market. Hackers may also hijack website accounts to redirect traffic to other websites that contain malware or are selling counterfeit goods.
In some cases, attackers will hold a website hostage and demand a ransom from the owner to regain access to their site. This is known as ransomware.
The level of risk will depend on what your website does. If you run an e-commerce website, you will be at a higher risk of attack because hackers can steal personal and credit card information. The risk is primarily reputational if you have a simple informational website. However, any website can be hacked, and no one is immune from attack.
Types of attacks
Cross-Site Scripting (XSS)
XSS is an attack that allows the attacker to execute malicious scripts in the victim's browser. This can hijack the user's session, redirect the user to a malicious site, or steal sensitive information.
Injections Attacks
SQL injection is another attack where the attacker attempts to inject SQL code into a web application. If successful, the attacker can gain access to sensitive data or even take control of the database server.
How to prevent SQL Injection Attacks
There are a few simple steps you can take to prevent SQL injection attacks:
- Use parameterized queries. This ensures that the data entered by the user is treated as a parameter and not as part of the SQL code.
- Parameterized queries. This ensures that the data entered by the user is treated as a parameter and not as part of the SQL code.
- Validate all user input. Ensure it conforms to the expected format (e.g., is a valid email address) and is not longer than the maximum length.
- Use an input allowlist. This is a list of characters that are allowed in the input. All other characters are rejected.
- Escaping all user-supplied input. This replaces special characters in the input with escape characters that the SQL interpreter cannot execute.
Fuzzing (or Fuzz Testing)
Fuzzing is a type of attack that involves feeding invalid or unexpected data to a program to make it crash. This can be used to find vulnerabilities in the software or to Denial of Service (DoS) attacks.
How to Prevent Fuzzing Attacks?
There are several ways you can prevent fuzzing attacks:
- Use a web application firewall (WAF)
- Input validation
- Sanitization
- Escaping
Zero-Day Attack
A zero-day attack is an attack that exploits a previously unknown vulnerability. Tspecializedrticularly dangerous because the victim has no way to defend against them. Zero-day attacks can be used to take control of systems, install malware, or steal sensitive data.
How to Prevent Zero-Day Attacks?
The best way to prevent zero-day attacks is to keep your software up-to-date. This includes patching any known vulnerabilities and updating to the latest software version.
Additionally, you can use a web application firewall (WAF) to help protect against zero-day attacks. A WAF can detect and block attempts to exploit vulnerabilities, even if
Path (or Directory) Traversal
Path traversal is an attack that allows the attacker to access files and directories that they should not have access to. This can be used to gain access to sensitive information or to launch further attacks.
How to Prevent Path Traversal Attacks?
There are a few steps you can take to prevent path traversal attacks:
- Restrict access to sensitive files and directories.
- Use input validation. This ensures that the data the user enters is valid and does not allow access to restricted areas.
- Use an output allowlist. This is a list of characters that are allowed in the output. All other characters are rejected.
- Escaping all user-supplied input. This replaces special characters in the input with escape characters that cannot be executed by the server.
Distributed Denial-of-Service (DDoS)
A DDoS attack is an attempt to make a website or service unavailable by overwhelming it with traffic from multiple sources. DDoS attacks are often used to shut down websites or services or to make them slow and unusable.
How to Prevent DDoS Attacks?
There are several ways you can prevent DDoS attacks:
- Use a DDoS protection service - such as CloudFlare
- Limit the amount of traffic your website or service can handle
- Use rate limiting
- Filter traffic by IP address
Man-In-The-Middle Attack
A Man-In-The-Middle (MITM) attack is where the attacker intercepts communication between two parties. The attacker can then read, modify, or delete the exchanged data. MITM attacks can steal sensitive information, such as login credentials or financial information.
How to Prevent Man-In-The-Middle Attacks?
There are several ways you can prevent Man-In-The-Middle attacks:
- Use SSL/TLS encryption
- Use authenticated connections
- Verify certificates and signatures
Brute Force Attack
A brute force attack attempts to guess passwords or encryption keys by trying every possible combination. Brute force attacks can gain access to systems, networks, or data. They can also be used to crack encryption keys and passwords.
How to Prevent Brute Force Attacks?
There are several ways you can prevent brute force attacks:
- Use strong passwords and encryption keys
- Use multi-factor authentication
- Limit the number of failed login attempts
- Use a CAPTCHA or other security measure to prevent automated guessing
Using Unknown or Third-Party Code
There is always a risk when using code from unknown or untrusted sources. This code could contain vulnerabilities that attackers can exploit. Additionally, this code could be malicious and be used to perform attacks, such as data theft or denial of service.
Using only code from trusted sources is essential to help prevent these attacks. Additionally, you should review the code for any potential vulnerabilities before using it.
Additionally, third-party scripts should be hosted internally rather than externally (i.e. on a public CDN), as there is a risk that the code could be maliciously modified, with you being aware.
Website Risk Assessment - Penetration Testing
Cyber attacks can have a significant impact on businesses of all sizes. It is essential to assess the risk of a cyber attack and put measures in place to prevent or mitigate the impact of an attack.
A relatively straightforward first step is to use a free (simple) scan (Website Penetration Test): https://pentest-tools.com/website-vulnerability-scanning/website-scanner
The penetration test can output will be a report containing findings categories as:
- Critical
- High
- Medium
- Low
- Informational
The report will also include details of the finding, how to produce them and recommended actions to mitigate the risks.
- Work with an independent security partner.
- These tools are the same tools that hackers are using to find exploits – you should get there before they do
- Assess whether you internally have sufficient awareness and training on website security and how it fits in with your larger cybersecurity plan.
Active and Passive Scans
Passive Penetration Test
In a passive penetration test, the tester observes and analyzes the target system or network without actively engaging. The objective is to gather information and assess vulnerabilities without directly interacting with the target. The tester typically uses non-intrusive techniques such as network sniffing, traffic analysis, and reconnaissance to identify potential weaknesses. Additionally, in some cases, a passive penetration test may involve reviewing the source code of applications or systems to uncover vulnerabilities and assess the security of the codebase.
Advantages of passive penetration testing include:
- It does not disrupt the target system or network since there is no active probing or exploitation.
- It can provide valuable insights into the target's security posture without triggering any alerts or defensive mechanisms.
- It can help identify potential vulnerabilities and misconfigurations that may be visible externally.
- In the case of source code review, it allows for a thorough examination of the code to identify potential security flaws and weaknesses.
However, passive tests have limitations as they cannot provide a comprehensive assessment of a system's security since they don't actively exploit vulnerabilities or test the effectiveness of security controls.
Active Penetration Test
An active penetration test involves actively attempting to exploit vulnerabilities and gain unauthorized access to the target system or network. The tester simulates real-world attacks by actively probing and interacting with the target to identify vulnerabilities and assess the effectiveness of security controls. This type of test requires the tester to have explicit permission to conduct the assessment.
Advantages of active penetration testing include:
- It provides a more comprehensive evaluation of the target's security posture by actively probing and attempting to exploit vulnerabilities.
- It helps identify vulnerabilities that may not be evident through passive techniques.
- It tests the effectiveness of security controls, incident response mechanisms, and the overall resilience of the target system or network.
However, active tests have certain considerations:
- They risk inadvertently causing disruptions or damaging the target system or network if not conducted carefully.
- They may trigger security alerts or defensive mechanisms, which could lead to false positives or false negatives if the response is not properly managed.
- Due to their active nature, they require explicit permission and coordination with the organization responsible for the target system or network.
It's important to note that passive and active penetration testing serve different purposes and can be used together to assess a system's security comprehensively. The choice of which type to use depends on the testing scenario's specific objectives, resources, and constraints.
Understanding the results is not straightforward. Understanding the results of a security report is not straightforward due to the complexity of the findings and the technical nature of the information presented. Security reports often contain detailed information about vulnerabilities, their severity, and potential risks to the target system or network. Interpreting and comprehending this information requires a strong understanding of security concepts, technical terminology, and the context in which the assessment was conducted.
Moreover, security reports may include technical details, such as exploit techniques, vulnerability descriptions, and recommendations for remediation. Without a solid background in security and a familiarity with the specific technologies and systems being assessed, it can be challenging to grasp the implications and significance of the reported vulnerabilities fully.
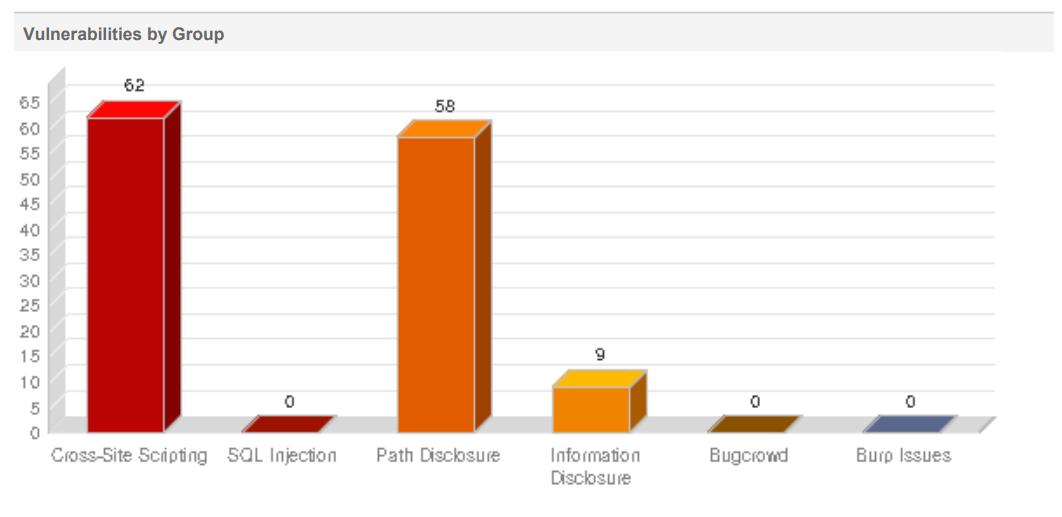
To address this issue, security reports should ideally be accompanied by clear and concise explanations that provide context, prioritize the findings based on their impact, and offer actionable recommendations for remediation. Visual aids, such as graphs, charts, and summaries, can also help to convey the key findings in a more accessible manner.
Additionally, it is beneficial to involve stakeholders knowledgeable about the target system or network in reviewing and interpreting the security report. This can include system administrators, IT personnel, or security experts who can provide valuable insights and context to understand the findings' implications better and prioritize remediation efforts.
Overall, it is essential to approach security reports with a focused mindset, seeking clarity and guidance from knowledgeable individuals to fully comprehend the results and make informed decisions regarding mitigating identified vulnerabilities.
How to mitigate the risk
- Identify the effort to resolve findings – prioritizing the critical and high.
- Produce and implement a correction plan, followed by a rescan.
- Ensure that your development partner is aware of your ongoing organization security requirements.
Consider your CMS Platform
Is your CMS supporting your security requirements? If not, you should consider changing to a more secure platform.
Some of the things you should consider when choosing a CMS platform from a security perspective include:
- How easy is it to keep the software up-to-date?
- Are there well-documented security procedures?
- What kind of encryption does the CMS use?
- Maybe it is challenging to resolve security issues on your current CMS platform.
- Consider transitioning to a secure CMS platform.
What’s Good About an Open Source CMS
An Open-Source CMS is one where the source code is made freely available and may be redistributed and/or modified.
The most popular CMS by far is WordPress. WordPress has a vast community and user base - 62% of the CMS Market Share (455M WordPress sites globally as of 2021). WordPress powers thirteen times more CMS websites than Joomla, the second most popular CMS host.
There is also a low initial cost of ownership, as WordPress is free and open-source software released under the GPL. You can download it from wordpress.org, as well as find a vast range of plugins and themes to extend its functionality.
Additionally, WordPress is relatively easy to use and manage, even for those with little technical knowledge. The backend interface is user-friendly and intuitive, and there is a wealth of online documentation and support available.
What’s Not Good About Open Source
- Huge insecurity – it is difficult to identify who developed the open-source software, and there are no guarantees in terms of security, support and performance
- Over 99% of WordPress vulnerabilities are related to plugins or themes. (Source)
- 29% of the WordPress plugins with critical vulnerabilities reported in 2021 received no patch from their developers. (Source: The State Of WordPress Security 2021)
- “Open source is free” – not really; while the license is free, the total cost of ownership can be much higher due to lower stability, missing professional support, the complexity of using multiple add-ons and complex upgrades that may even require rewriting your website for the new version
What’s the Alternative to Open Source
A proprietary CMS keeps the source code closed from the public, which generally results in a more secure platform. A proprietary CMS is developed, maintained and supported by a single vendor.
Typically, licensing is more expensive for a proprietary CMS. But the trade-off is that you get a more stable platform with professional support, saving you money in the long run.
Proprietary systems also offer an easier path to compliance with regulations like GDPR and CCPA. As these regulations evolve, your vendor will be on top of them and offer updates to the platform so you can stay compliant without incurring additional costs.
Additionally, as proprietary CMS is supported by a single vendor (not the community), it will offer a single point of contact in case you need assistance. Many will provide support and SLAs for security issues. For example, Kentico provides 24/7 support and 7-day bug fixing as standard.
An all-in-one DXP will not rely on Plug-ins to provide complete functionality ‘out of the box'. From a security perspective, the advantage is that you will have a limited number of ‘moving parts’ and a smaller attack surface. The other advantage is that it will be easier to keep these ‘moving parts’ up-to-date with the latest security patches.
A DXP should provide an eCommerce platform, Web Content Management System (CMS), Digital Marketing tools, Customer Relationship Management (CRM), and a central Portal. As it is an all-in-one platform, it should provide 'best of breed' functionality for each of these disciplines, making it easier to effectively meet your customer’s needs.
Platforms are regularly security scanned by the vendor – for example, Kentico runs weekly penetration testing security scans on their platform using various providers.
Vendors will have a security-first mindset and build security into the development process. This way, they can avoid vulnerabilities instead of trying to patch them after they’ve been exploited.
Other Considerations
Any 3rd Party Systems your website is connected to? Are these secure, as they could be a gateway to the site?
- Analytics / Tracking (Google Analytics, HotJar)
- CRM (HubSpot, Salesforce, MS Dynamics)
- ERP (Xero, Stripe)
- Is your Domain Hosting protected?
- MFA-enabled for individuals
- How are Leavers/Joiners to your organisation handled?
- Users sharing passwords
- Accidentally service suspension / Renewal Credit Card details up to date
What to do if your website is attacked?
- Change your passwords - If your site's been hacked, you need to change all your passwords immediately.
- Remove the hack - It's nearly impossible for anyone to remove malware from a website by hand reliably. To remove the compromise from your files, we recommend using a service like Website Security.
- Identify & fix the weakness - To prevent your site from getting hacked again, you should identify how your site was compromised. There are two types of weaknesses: passwords and structural problems.
- Restore from backup - If you have a backup of your website (and database) that you know wasn't corrupted, you should re-upload it to your hosting account.
- Communication - Promptly inform your employees, website users and relevant regulations of the current situation.
- Learnings - Put systems and processes in place to improve website security and avoid future breaches
Marathon, not a sprint
Best to be prepared and already have a partner from whom you can get assistance from
- This is not a one-off exercise.
- Repeat scanning at least once a quarter (for new vulnerabilities)
- And each time there is a sizeable website code change
- Awareness and Training of all employees is essential
In Conclusion
Your website is one of your most important business assets. It’s the face of your company and often the first impression people have of you. That is why ensuring your website's security is so critical. Unfortunately, website attacks are on the rise and can devastate a business. We hope this article has given you a better understanding of website security and how to protect yourself from attacks.
Please don't hesitate to reach out if you have any questions or would like to chat about your specific situation. We want to help you keep your business safe online!
Related Resources
Blogs
- https://www.kentico.com/discover/blog/how-to-prevent-the-devastating-impact-of-a-data-breach-with-kentico-xperience
- https://www.kentico.com/discover/blog/choose-kentico-xperience-for-security-and-peace-of-mind
